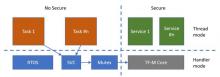
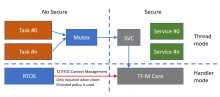
When using TF-M on v8-M with Secure Function Call SFC (aka Library) mode, the entry to the secure side is protected by a Mutex.
Thus only one thread at the time is calling a secure service. The picture below should therefore represent the execution flow (Level 1 isolation).
Under this assumption there is no need to implement TZ_context management in the RTOS (https://arm-software.github.io/CMSIS_5/Core/html/using_TrustZone_pg.html#RTOS_TrustZone). Any RTOS could be used, provided that the Mutex capability is sufficient.
Moreover this design should create a really simple secure side:
- Only one stack is needed on the secure side for Thread mode execution
- No multi-threading issues that need to be resolved (i.e. with access of hardware crypto accelerators)
The drawback of course is that only one task at a time can use a secure service. However an RTOS with priority inversion will ensure that the Secure service is executed as fast as possible, once a scheduling conflict arises.
I would like to gather feedback on that approach. Let me know what you think.