Proof Of Concepts
This page gives information on the Proof Of Concepts (PoCs) based on Trusted Firmware-M (TF-M). It demonstrates Non-Secure Applications availing Secure Services in Trusted Firmware.
The PoC have been demonstrated at various events such as ELC at Edinburgh, Linaro Connect at Vancouver.
1. Pelion Client using TF-M
The PoC is done on a MuscaA board.
One of the Cortex-M33 processor on the MuscaA board runs Trusted Firmware-M on the Secure domain and Pelion client on the Non-Secure domain. mbedOS is the RTOS running on the Non-Secure domain.
The PSK credentials are stored in the Secure domain using the TF-M Secure Storage (SST) service. Pelion client fetches these credentials for establishing secure connection to Pelion portal. Resources (e.g. LED) on board can be accessed using the get/put/post methods over the internet through the Mbed cloud portal, the duration can be changed through pattern resource.
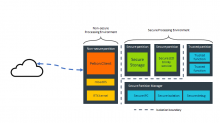
Here is a functional block diagram showing the components involved in the PoC.
Using Secure Storage Service
1.Mbed cloud app fetches PSK from Secure Storage in TFM
2.Keys are used to secure the communication between client and Pelion portal
3.App uses the IP stack (TCP) for communicating with the internet
4.Connection is established between the client and Pelion portal. Client is registered with the portal
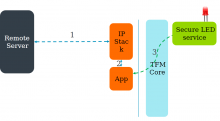
Using Secure LED Service
1.Remote server initiates get/put/post commands for resources over internet
2.Pelion client receives these commands
3.Mbed cloud app uses secure LED service to blink the LED in a predetermined pattern.
This Proof Of Concept was shown as a Demonstration at ELC-E in Edinburgh in October 2018.
The sensor on the MuscaA board was used to detect the motion of a Robot. The motion information was sent to Pelion Portal using the Secure connection established as described above. The Pelion Portal displays the motion information on a graph as shown in this video Demo
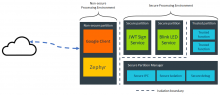
2. Google IoT Client using TF-M
The PoC is done on a MuscaA board.
One of the Cortex-M33 processor on the MuscaA board runs Trusted Firmware-M on the Secure domain and Google IoT client on the Non-Secure domain. Zephyr is the RTOS running on the Non-Secure domain.
The client requires signed JWT (JSON Web Tokens) to perform handshake with Google MQTT server. The Client running on the Non-Secure side uses JWT sign service in TF-M for signing the token securely. A blink LED secure service in TF-M is invoked whenever the client talks to the service.
Steps:
- After secure boot, Trusted Firmware runs in Secure space and jumps to Zephyr.
- Zephyr start in Non-Secure. Connect to google server by TCP with TLS handshake
- Call secure service from Zephyr to TFM for JWT sign
- Connect to MQTT server and subscribe the device config topic
- Get the latest configuration from server and publish device status periodically
- Blink LED by calling secure service when talking with server
- Last Author
- cringti
- Last Edited
- Aug 9 2022, 4:55 PM
Event Timeline
<a href="https://repomod.com/" data-hook="WebLink"><span>repo mod</span></a> we offer a variety of mods designed to take your gameplay to the next level. Whether you're looking to add new roles, increase the number of players, or boost your stamina, we've got you covered. Our popular mods include R.E.P.O. Roles, R.E.P.O. MorePlayers, R.E.P.O. MoreStamina, ShrinkerCart, Enemy Location, LegoGnomes, EvenMoreHead, and InfiniteEnergyCrystals. Dive in and explore the endless possibilities with REPO Mods!